We are proud to announce Topicus KeyHub 31. This release brings a variety of smaller and larger improvements throughout the entire suite. Two of the most notable usability improvements are: support for auditing nested groups together with the group they are nested under, and the addition of OAuth2 application profiles and what this does to the CLI.
OAuth2 application profiles
TKH-1817 OAuth2 applications now have a profile that describes how this application deals with secrets and tokens. The profiles are based on the application profiles described in the OAuth2.1 draft specification. They define if an application gets assigned a client secret and whether it will receive refresh tokens and how long such a refresh token will be valid. This will allow applications to remain authenticated for longer, without the need for the user to re-authenticate, while still remaining secure. The CLI has been enhanced to make full use of this new feature and now allows multiple concurrent authenticated sessions, which can potentially stay authenticated indefinitely.
Please note that during the upgrade, profiles are automatically assigned on a best effort basis. It is recommended to review the assigned values after upgrading to Topicus KeyHub 31.
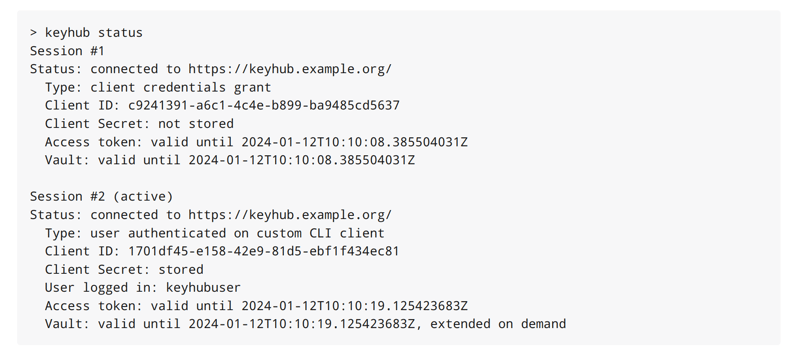
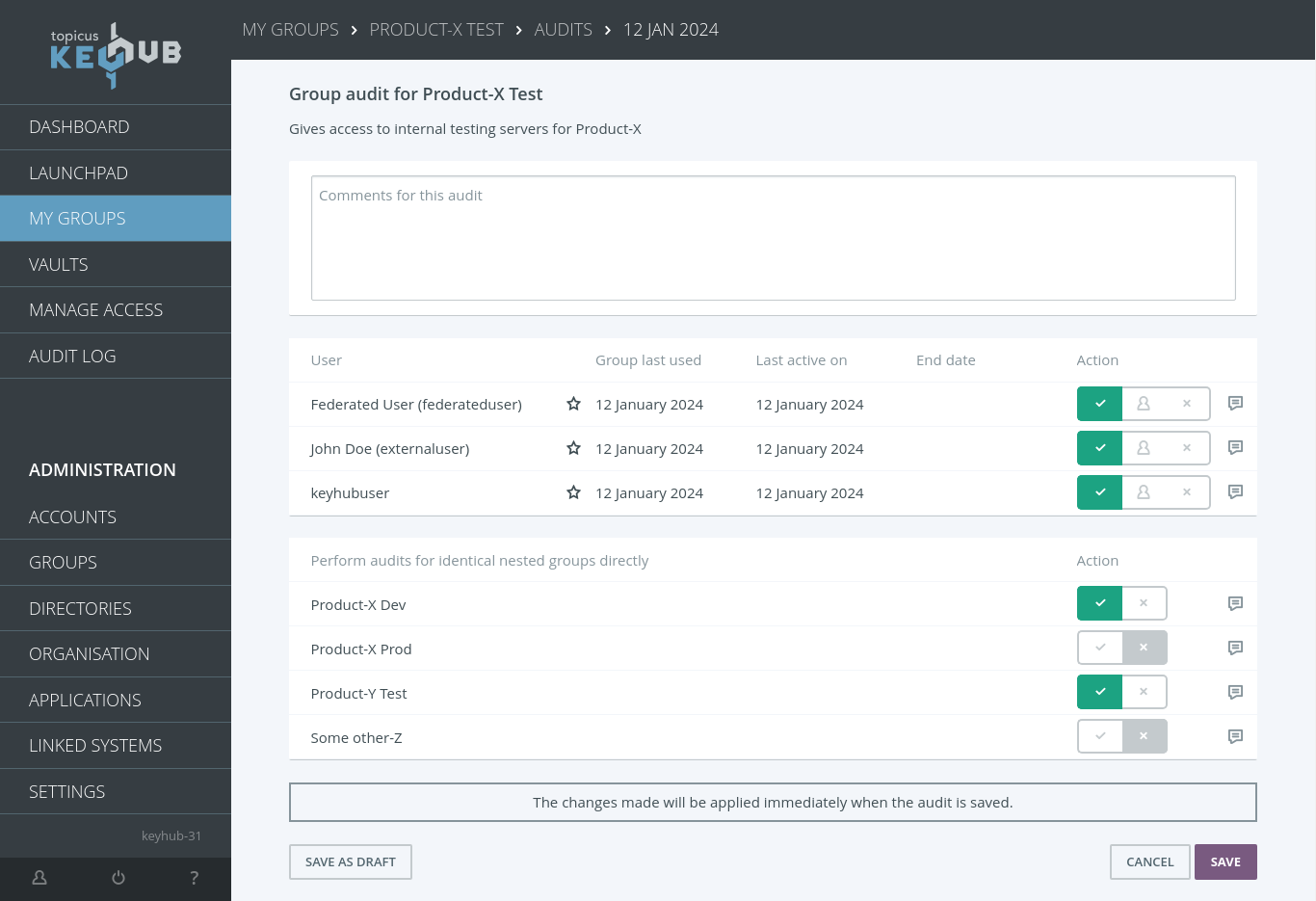
Auditing groups with nested groups
TKH-2068 When a group has multiple nested groups, all of which contain only memberships resulting from this nesting, auditing could be very cumbersome. In Topicus KeyHub 31 this is no longer the case. During the audit, the manager can opt to automatically audit all nested groups (as long as the groups only contain nested members). This effectively allows you to audit many groups at once. Of course, all of this is recorded in the audit for future reference.
Assorted improvements
The following larger and smaller improvements and bug fixes were made:
-
TKH-2463Metrics were added for the state of linked systems. -
TKH-2495Some fields in the licenses that have never been used were removed. -
TKH-2523Service accounts are now also scoped on organizational unit. -
TKH-2579Client applications are now allowed to also read private groups when given the permission to query groups. -
TKH-2592Checks were added to linked systems and namespaces to make sure they do not provision in the same or overlapping DNs. -
TKH-2620It is now possible to use some wildcards in the whitelist for OAuth2 resource indicators, analogous to redirect URIs. -
TKH-2627The selection for setting up new group authorizations will no longer show options that are already set on the selected group. -
TKH-2630TKH-2718The script engine for evaluating custom attributes was migrated to isolated-vm. -
TKH-2635Back-navigation from vault records now correctly returns the dashboard when expected. -
TKH-2642Creating multiple vault records at the same time using automation no longer gives an error. -
TKH-2643The button to move an internal account is now only visible after the account has been created. -
TKH-2644The filename for vault exports now contains the name of the exported vault. -
TKH-2645Handling of errors in the OAuth2 flows was improved in several places and now gives the correct responses to the client. -
TKH-2646The explanation of the auditor role in the manual was improved substantially. -
TKH-2649Screenshots were added to the manual about handling password recovery requests. -
TKH-2651Uniqueness of email addresses is now checked case insensitive. -
TKH-2653It is now possible to copy a password from the vault record detail screen without having to display it first. -
TKH-2654The action to rotate the IdP signing certificate has been moved to the appliance manager and now correctly syncs across all nodes in a cluster setup. -
TKH-2658The version of GraalVM used to build the native CLI was upgraded to 21. -
TKH-2659Metrics were added for jobs running in the appliance manager, such as backups and upgrades. -
TKH-2664The startup sequence of the application now correctly checks for all errors that might occur when upgrading the database. -
TKH-2666The status of a namespace now correctly reports the status of its base system. -
TKH-2667Processing a request to create a new group on system will now correctly send the appropriate email. -
TKH-2668Test coverage on some crypto migrations was improved. -
TKH-2669An error was fixed when a user tried to sign in multiple times concurrently. -
TKH-2671The self service options for linked systems now correctly check for all supported features of that linked system. -
TKH-2672Activating groups on the dashboard which require entering a reason could trigger an error. -
TKH-2673An error was fixed when searching on the vaults page with a locked vault. -
TKH-2674An error was fixed when trying to search for accounts with an invalid identifier. -
TKH-2675The email that is sent when accepting a password reset would trigger an error. -
TKH-2676Long running OS updates no longer cause a timeout during the upgrade. -
TKH-2680Backups created in a single node setup can now be restored on a cluster. -
TKH-2681Some web resources could be cached by the browser when they should not be. -
TKH-2682Reporting of CSP violations was disabled as these are all covered in tests and were resulting in lots of false positives, mostly caused by installed browser extensions. -
TKH-2683Fields containing sensitive data are now marked in the OpenAPI specification. -
TKH-2684The from email address is no longer set to that of the user for notifications triggered by the user himself. -
TKH-2685It is now possible to directly give permissions to other clients when creating new groups via a client (i.e. via Terraform). -
TKH-2686A textual change was made to the emails for confirmation of new internal accounts. -
TKH-2689Pgpool II was upgraded to version 4.5.0. -
TKH-2690Opening a linked Active Directory via administration would trigger an error. -
TKH-2691Exporting many groups via the auditor dashboard would take a very long time and could even trigger a transaction timeout. -
TKH-2692Metrics were added about the latency for database calls. -
TKH-2693The healthcheck for application container was fixed to only check liveness. -
TKH-2694Pac4j was upgraded to version 6.0.0. -
TKH-2698The OAuth2 device code flow now more strictly checks its parameters. -
TKH-2699Handling of OAuth2 refresh tokens was improved significantly. -
TKH-2700Audit records were added for changes to global settings. -
TKH-2702Some actions could trigger repeated invalidations of the authorization cache, causing these actions to take much longer than required. -
TKH-2703Enabling a linked system that did not have an external UUID set would give an error. -
TKH-2706Error handling for submitting an audit was improved. -
TKH-2709The layout of tables under administration on a phone was improved somewhat. -
TKH-2711Testing a namespace on an LDAP no longer gives an error. -
TKH-2713An error was fixed that would cause the native CLI to crash when trying to login. -
TKH-2717During an upgrade in a clustered setup, some nodes might not reboot while a reboot was actually required to complete the upgrade. -
TKH-2728Enabling SSH password authentication did not work correctly in non-clustered setups.

