We are proud to announce Topicus KeyHub 29. We've added a lot of extra functionality to vaults, but also performed upgrades to our underlying infrastructure.
As per usual, a number of assorted improvements and bug fixes are also included.
Upgrade to WildFly 29 and Jakarta EE 10
TKH-2277 We've upgraded our underlying infrastructure to keep up with the continuous development in the software landscape. With the upgrade to WildFly version 29.0.1 we've added just shy of 2 years worth of development and improvements to our codebase.
Jakarta EE has been updated to version 10 to comply with the latest (API) specifications and Jakarta namespace changes.
Upgrades like these are difficult to perform, as they tend to consume a lot of time and resources, but are necessary to keep in sync with the ongoing development and (possible) security fixes.
Improved telemetry endpoint
TKH-1475 TKH-2570 With the upgrade to WildFly 29, we felt it was the appropriate moment to improve our telemetry endpoint to provide more detailed information for monitoring.
We've built a new docker container that collects the telemetry from the various internal sources and provides a centralised endpoint to obtain the combined telemetries.
With the improved endpoint, it's now possible to actively push the telemetry using OTLP instead of passively pulling it. This is more efficient and reliable.
Please note that some metric labels have changed in the new endpoint, it's recommended to check your dashboard, to see if the received data is still being shown in the correct places.
Improvements to vaults
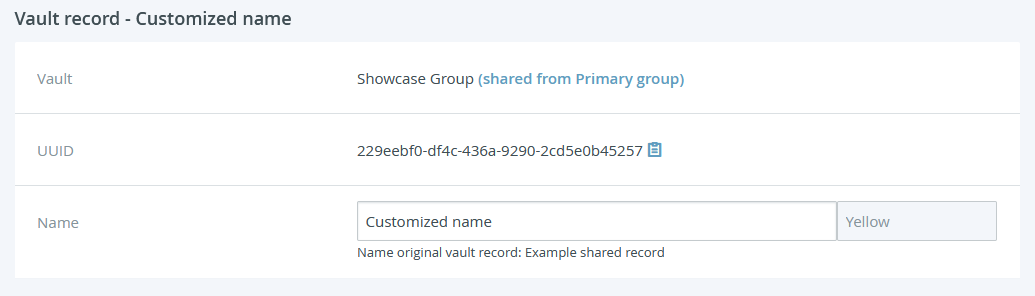
TKH-2235 The receiver of a shared record is now able to customise the name of their copy, this name will be retained when the parent record gets updated. If customised, the original record name will be displayed underneath the customised name on the vault record detail page.
TKH-2494 You can now share vault group records when using a client credentials grant to authenticate to the API.
TKH-2596 We've added the ability to export vault records, exports can only be performed on a personal vault or on a group's vault if you're a manager of said group.
TKH-2599 It's now possible to configure the password generator to meet your company policies. The default generator remains the very strong generator we always provided.
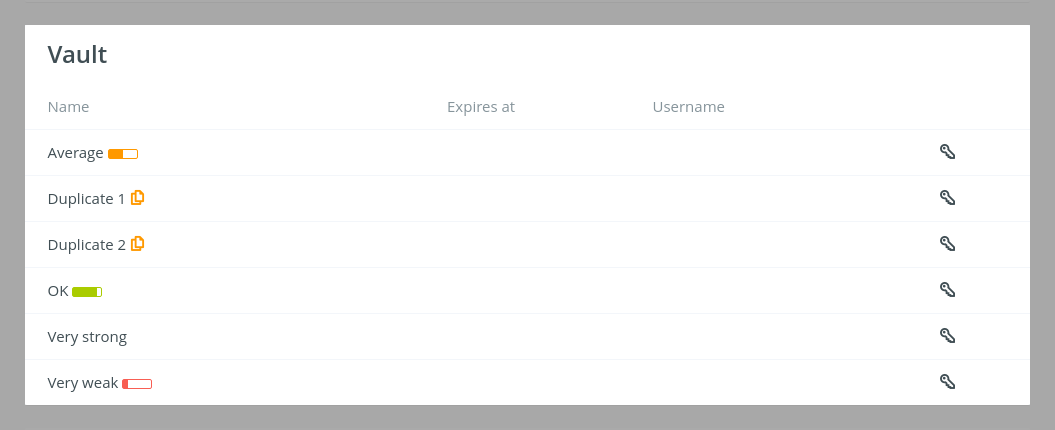
TKH-2600 We've added a strength indicator for the complexity of a password from a vault record and a visual marker for duplicate passwords within the same vault.
These indicators are encrypted before they are stored in the database, so in the event that someone were to have access to your database they wouldn't be able to use these indicators to find weak passwords.
Assorted improvements
The following larger and smaller improvements and bug fixes were made:
-
TKH-2571The read-only view of an application no longer shows "None" when custom attributes have been set. -
TKH-2575Combining delegated group management with nesting is no longer allowed. -
TKH-2577When transferring the ownership of a group on system, organisational units are now taken into account. -
TKH-2593Some obsolete sentences were removed from the manual. -
TKH-2595We've further extended our OpenAPI specification to suite the Go SDK and Terraform provider generation. -
TKH-2597We've reduced the time it takes to log in to KeyHub when being part of many groups. Also some logging was added to gain deeper insight on what happens during validation and signing at log in. -
TKH-2602The "delete" button was made visible on group records that are shared to a personal vault. -
TKH-2603The warning that is shown when revoking a group's access to an application was rephrased. It now states that the link between the group and the application will be deleted, rather than deleting the entire application. -
TKH-2604The option to promote a nested group member to a manager is no longer visible. The user's membership needs to be disconnected from nesting in order to be able to modify the role.

