Just before the summer holidays we are proud to announce Topicus KeyHub 27. This release focuses on delegating group manager privileges, continuing our work on organisational units and optimizing our openapi spec in preparation to facilitate client generation. As usual, a number of assorted smaller changes and bug fixes are also included.
Delegated group manager privileges
Our customers occasionally express a desire to have some groups' membership responsibilities (partially) managed by people who are not themselves members of that group. In earlier versions we introduced the authorizing groups for membership and audits, to give some control over membership to outside groups while still keeping the group manager front and center in this process.
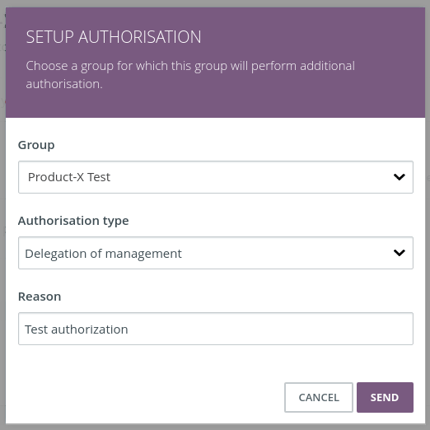
In this release, we went one step further and we introduce the ability to delegate a group's manager privileges as pertaining to group membership. Another group can be designated for delegation of manager privileges. All members of the designated group are granted these delegated privileges. This allows the members of this group to perform management for the group without being a member of the group themselves.
Specifically, it allows them to perform the following operations:
-
Add, remove or edit group members.
-
Edit group properties.
-
Perform audits on the members of the group.
To prevent the delegated privileges group from becoming too much of a concentration of rights, it is mandatory to set up an authorizing group for membership before delegated manager privileges can be issued. Any change in the members of the group must therefore be additionally approved. It is also not possible for users to try to add themselves to the group.
The following tickets for group delegation were implemented:
-
TKH-2301It is now possible to delegate group manager privileges to another group. -
TKH-2490An option was added to group classifications to make group manager delegation mandatory. -
TKH-2491It is now possible to set group manager delegation at group creation time for OAuth2 clients. -
TKH-2529Rotating vault keys for groups should no longer possibly result in an error if any authorisation other than delegation is set.
Organisational units
We've continued our development on organisational units. With this release it is possible to link provisioned systems to an organisational unit and restrict what groups can request a group on the system. The area of focus for organisational units for the upcoming releases will continue to be provisioning.
The following tickets related to organisational units were resolved:
-
TKH-2442Provisioned systems can now be scoped to an organisational unit subtree. -
TKH-2512TKH-2513TKH-2514We've fixed various issues related to creating new groups and adding members, where the organisational unit's scoping was not taken into account. -
TKH-2520An account directory's helpdesk group should always belong to the account directory's organisational unit. -
TKH-2531A missing translation was added for 'create new group'-requests. -
TKH-2526The default organisational unit for KeyHub admins is now the root organisational unit.
Assorted improvements
The following larger and smaller improvements and bug fixes were made:
-
TKH-879To avoid confusion, an informational message is now displayed on pages such as "My Groups" when there is no data (yet) to display. -
TKH-1327KeyHub now stores the used service contract versions per OAuth2 client and shows a notification if a client uses an outdated service contract version. -
TKH-2200TKH-2516TKH-2521Various improvements have been made to our OpenAPI spec to better facilitate client generation. -
TKH-2257We've reworked our touch-locking code to avoid deadlocks and concurrent modification errors, especially when sending parallel requests from a client. -
TKH-2401Internal accounts can now be moved to another directory. Note that this may result in changes to their organisational unit memberships. -
TKH-2413We fixed a bug in our code related to multiple session from different IP-adresses. KeyHub should now no longer request authentication more often if you regularly switch between IP-adresses, as long as you're still using the same device and browser. -
TKH-2469Cancelling a request now results in an e-mail being sent to possible approvers to inform them of this. This avoids confusion about seemingly disappeared requests. -
TKH-2470It is now possible to export the groups on system a service accounts has access to from the auditor dashboard. -
TKH-2471Selfservice can now be disabled for a provisioned system, so that group managers can't initiate requests for groups on system by themselves. -
TKH-2481Reviewing a group's audit, where that audit contains changes to group memberships, should now always work even if the reviewer is not a member of the group being reviewed. -
TKH-2484TKH-2510We fixed a visual bug that could hide the top-most auditrecord in Firefox. -
TKH-2485To facilitate the review process of our browser extension, we now also package a source zip-file. -
TKH-2487It is now once again possible to use the keyboard to scroll through the search results list in the KeyHub browser extension autofill menu. -
TKH-2488When searching vault records in the browser extension, we should once again search case-insensitive. -
TKH-2489TKH-2507We've improved handling of non-standard login forms by the browser extension. -
TKH-2492Most groups on system have are used by only one group. We've changed the default in the 'request group on system'-dialog to "request new group on system" to reflect this. -
TKH-2493When requesting a new group on system as a group manager, via the Manage Access page, the new group on system's name is now once again prefilled with an autogenerated suggestion. -
TKH-2496We've improved our interaction with AWS when running on the AWS platform without a public ip address. -
TKH-2498After logging in in a separate browser tab, the browser extension should once again return you to your previous tab, instead of to the rightmost tab. -
TKH-2500We've improved input validation so you can no longer try to create a support dump for a future date. -
TKH-2501After succesfully submitting our browser extension for Safari to the App Store, we've now also added a direct link on the profile page. -
TKH-2502Updating KeyHub while certain scheduled tasks are running should no longer result in errors in the appliance manager. -
TKH-2503There is now a release channel for nightly development builds. -
TKH-2504We ignore signature validation errors caused by concurrent modifications on the relevant entity. -
TKH-2505We added translations for all license validation errors to avoid hard errors even if an installation ends up in a state it should not be able to end up in. -
TKH-2506Updating KeyHub should no longer be able to generate errors relating to the cleaning of temporary files. -
TKH-2508We now explicitly support the 'email' scope for OIDC. -
TKH-2509We added a missing 'in-use' check for certain license features. -
TKH-2517We've improved the UI related to unfolding group folders on the dashboard. -
TKH-2519Invalid signature notifications relating the a group signing key are now only displayed to the group's managers, since only they can repair it. -
TKH-2525We've improved the handling of accents and non-ascii characters in provisioning. -
TKH-2527Invalid secret shares will now be silently deleted and recreated at a later time, to avoid blocking a user with errors they can't easily resolve. -
TKH-2534It is no longer possible to 'read' empty data from a vaultrecord in a vault that requires you to first activate the group before reading. -
TKH-2535TKH-2536We've fixed a few errors related to installing or upgrading KeyHub on various VM platforms. -
TKH-2539We've rewritten the vault recovery logic to better handle copied, moved, or shared records.

