We are extremely pleased to be able to announce the 17.0 release of Topicus KeyHub. This is the biggest release in years and is the payoff for many months of hard work. In this release we bring a first look at a high-availability setup for KeyHub, the ability to use FIDO2-compatible authenticators for 2FA and a first set of best-practice guides. As usual, a number of smaller improvements have been made and several issues have been fixed.
Note: Due to the size of the release, the update process can take longer than usual, up to 15 mins after creating the backup.
Security keys for 2FA
TKH-1010 We added support for the WebAuthn browser API, meaning you can now use modern FIDO2-compatible security keys such as produced by Yubico, Feitian and Google as 2FA. Simply go to your profile page and click on "Add security key" to get started.

Best practice guides
TKH-1533 We wrote a few best practice guides to help you in using KeyHub to its fullest. These range from setting up webhooks to push events to Splunk, to preparing and linking an AD to be provisioned by KeyHub, to setting up Devolutions Remote Desktop Manager to automatically retrieve your credentials from KeyHub.
The guide is available on our website and at the documentation page of your Topicus KeyHub installation: https://<YOUR_KEYHUB_URL>/docs
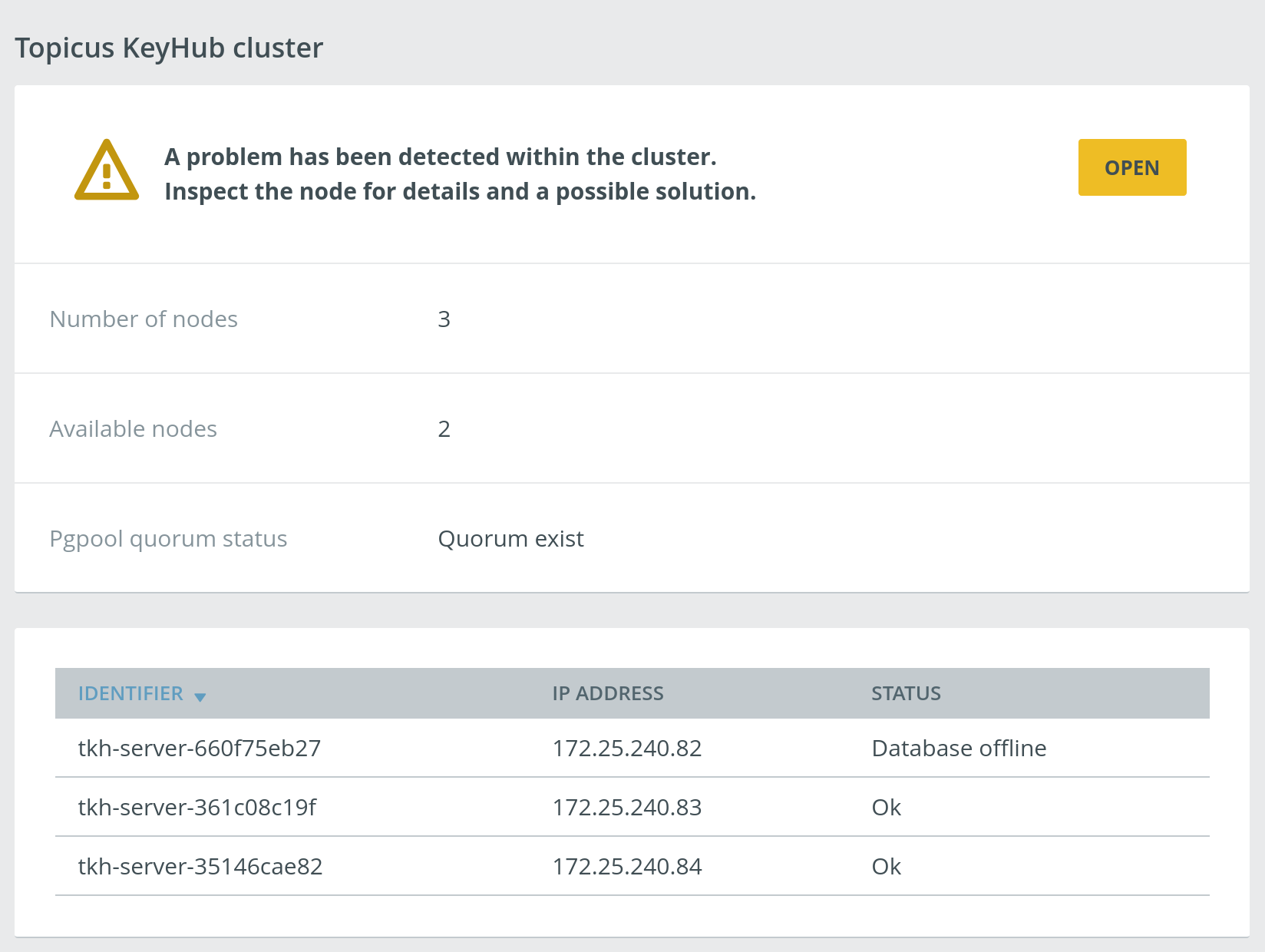
High-availability clustered setup
TKH-902 TKH-1540 With this release we bring a first look at a clustered setup for Topicus KeyHub! Through the appliance manager it is now possible to set up a cluster of Topicus KeyHub instances (we advise an odd number, e.g. 3). All services will run on all nodes, causing graceful degradation if one of the nodes were to fail.
Clustering Topicus KeyHub instances is still considered beta, meaning it has some rough edges, lacks certain features and may experience unexpected failures. Also, the documentation still has to be written. We advise everyone interested in such a setup to test it out on a test-environment and we welcome any feedback you have.
Small improvements
The following smaller improvements and bug fixes were made:
TKH-1423TKH-1514The overview of vault records on the Vaults page now shows if a record is shared with or from another vault, including the end date (when applicable).TKH-1455KeyHub should now accept all RFC 822-compliant email addresses.TKH-1478The auditor dashboard should now only report audits as overdue after the second tuesday of the month, instead of on.TKH-1489We fixed a bug where trying to re-authenticate against an OIDC-provider from within KeyHub would lead to an exception.TKH-1490Moving a manual launchpad tile no longer leaves a temporary "ghost" tile in the old group on the launchpad page.TKH-1491We dropped the "This group doesn't provide access to anything" marker since it was of questionable usefulness and generated false positives.TKH-1492We fixed a permissions bug where a member of the authorizing group could not authorize a group activation request unless they were also a member of the authorized group.TKH-1493The install wizard should no longer be able to get stuck on step 4.1TKH-1494We no longer try to sync up provisioned accounts across all linked systems every minute. This generated a lot of unnecessary load in cases where linked systems were unavailable for longer and/or frequent periods.TKH-1496TKH-1541Health and metrics endpoints are now available underhttps://<YOUR_KEYHUB_URL>:9443/healthandhttps://<YOUR_KEYHUB_URL>:9443/metricsTKH-1503The Topicus KeyHub CLI now gives an appropriate error message when its version does not match that of the server's.TKH-1506We introduced a landing page for OAuth flows with native apps. This way, the user does not end up "stuck" but gets a clear message that the login was successful and that they can close the page.TKH-1507The "external URL" field in the Topicus KeyHub installation wizard now properly checks that the provided URL does not contain a path.TKH-1508To prevent unnecessary vault resets, we now hide the "I completely forgot my password" checkbox on the first attempt when we detect the AD password has been changed outside of Topicus KeyHub.TKH-1510We upgraded our application server to Wildfly 21.TKH-1511You can now also use key pairs other than RSA (such as EC) for certificates.TKH-1512It is now possible to bulk import vault records from a CSV file.TKH-1525We added a confirmation dialog to the "restore backup" action in the management interface.TKH-1526We fixed a bug causing applying system updates to fail for specific updates.TKH-1527You should now be able to restore the oldest backup.TKH-1528CentOS was upgraded to version 7.9.TKH-1529The Python library used for backup encryption was replaced by a new implementation.TKH-1531Test cases now run more reliably when running multiple builds in parallel.TKH-1532A permission error was fixed when moving vault records using the CLI.TKH-1535The user's time zone was not selected correctly at step 2.1 of the installation.TKH-1537Using the option to generate a self signed certificate during the installation would cause the installation to fail at step 3.TKH-1538When performing 2FA in any other way than replying 'Yes' to the push message, the push message was not invalidated.TKH-1539Updates to SaltStack during the update of the Topicus KeyHub appliance are now handled more reliably.

