With the release of Topicus KeyHub 44, we are excited to announce major behind-the-scenes upgrades that enhance security. This version introduces a significant OS upgrade to AlmaLinux 9, bringing with it improved security through SELinux. In addition to these upgrades, we've focused on delivering new features and improvements to our Identity Lifecycle Management and Account Provisioning, including a new synchronization dashboard. This release also addresses long-standing user needs by introducing the ability to use multiple URLs for a single vault record. As always, we've also included a number of smaller improvements and fixes.
Important notices
Resolved security vulnerability
TKH-3516 This release contains an important security update. We have resolved a Server-Side Request Forgery (SSRF) vulnerability in an internal service.
It is important to note that this vulnerability does not allow an attacker to gain unauthorized access to data within your KeyHub environment. The actual risk is that an attacker with access to your KeyHub environment could abuse your server to send requests to other systems, potentially making your organization appear as the source of a Denial-of-Service (DoS) attack.
To eliminate this risk, we strongly advise upgrading to version 44. If you are unable to upgrade in the short term, please contact support to discuss alternative mitigation steps.
Manual OS upgrade to AlmaLinux 9
TKH-2482 This release features a major OS upgrade to AlmaLinux 9. This is a separate step that runs after the upgrade to Topicus KeyHub 44. When automatic updates are enabled, the upgrade will start automatically at the first scheduled update moment on or after November 24, 2025.
Due to technical limitations, the OS upgrade process cannot create a filesystem snapshot before starting the upgrade. Therefore, we recommend starting the upgrade to AlmaLinux 9 manually before November 24, 2025, and creating a full VM snapshot as a precaution.
See knowledge base article Upgrade to AlmaLinux 9 for more information.
TKH-940 As part of the above-mentioned OS upgrade, SELinux will be enabled on the VM. SELinux is a security layer in the Linux kernel that implements mandatory access control (MAC). This greatly enhances the security of the VM. We've performed extensive testing on the enforced policies to ensure compatibility with the services that run inside the VM.
However, due to the nature of these policies, it is impossible to guarantee compatibility with services that are outside our control, such as cloud management services and backup agents. If SELinux is causing issues with any of these services, it is possible to temporarily put it in permissive mode.
See knowledge base article Upgrade to AlmaLinux 9 for more information.
Identity Lifecycle Management and Account Provisioning
TKH-3254 TKH-3512 TKH-3513 A complete new dashboard was added to replace the simplistic flat synchronisation logs for linked systems. This dashboard shows reads, writes, warnings and errors for the past 48 hours on a specific system. It supports filtering to drill down on any potential issue and provides access to all logs, even for incremental synchronisations.
-
TKH-3359It is now possible to override the value of an attribute when an attribute rule allows this. -
TKH-3366The schedule at which the AFAS synchronisation runs can now be configured. -
TKH-3390Custom attributes can now optionally be configured for any access profile, not just access profiles that are linked to an account directory. -
TKH-3392An attribute rule can now claim exclusivity for an attribute, making it unavailable to other access profiles.
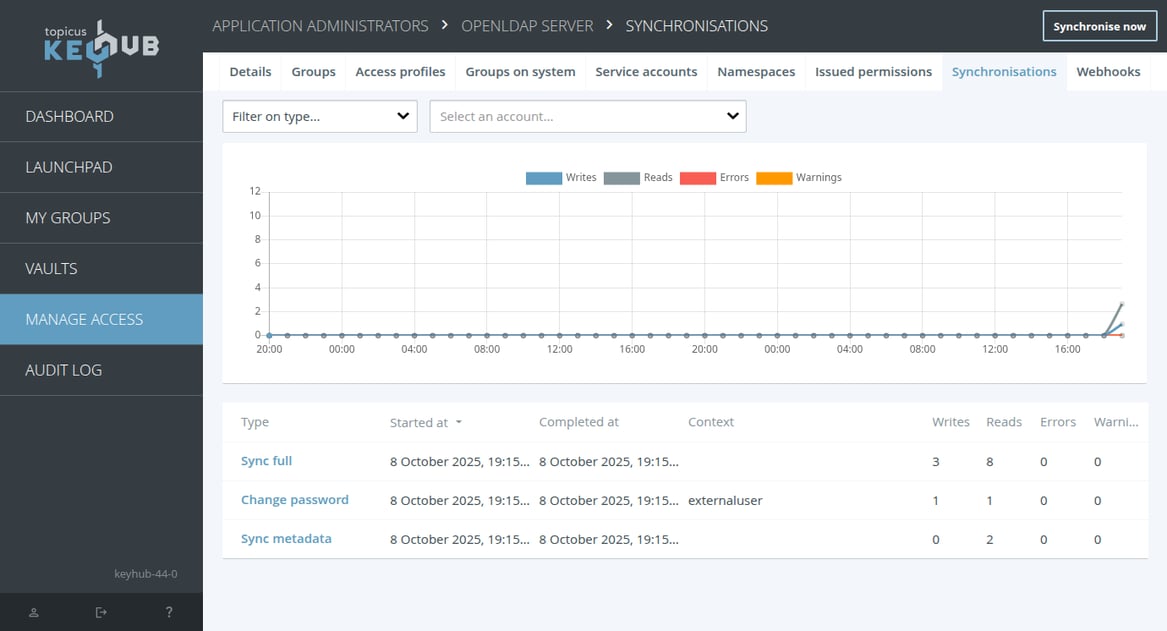
Synchronisations for a linked system
Multiple URLs for vault records
TKH-1445 Sometimes a web application has multiple URLs. In other cases the same underlying account is used via multiple frontends. In previous versions, you needed to create multiple records in the vault for this. In KeyHub 44 you will be able to define additional (secondary) URLs for a vault record. The browser extension will match the record if any of the URLs match. The primary URL will still be used as a link to the website.
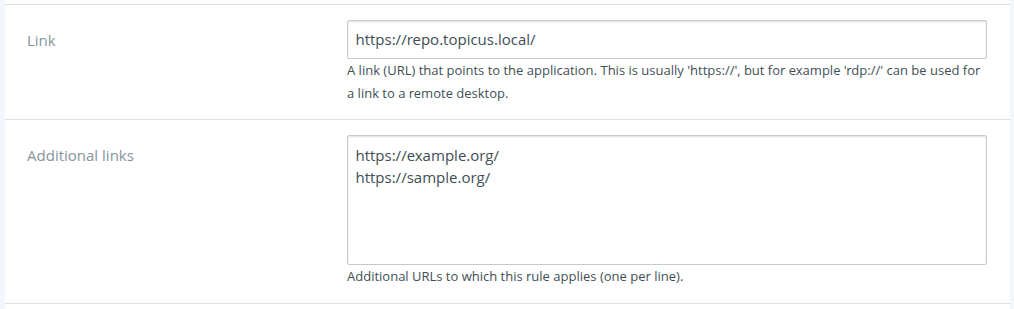
A vault record with multiple URLs
Assorted improvement
The following improvements and bug fixes, both large and small, were made:
-
TKH-2289Our licenses are now signed using ed25519. -
TKH-3142The Terraform provider now supports directly providing access to (linking) existing service accounts when creating a new group on system. -
TKH-3418Buttons to start updates on the dashboard of the appliance manager are now disabled when certain tasks, such as updates or backups, are running. -
TKH-3446The share button for a vault record is now hidden when activation of a group is required to access the vault. -
TKH-3451When deactivating a group, any open request to extend the activation is now cancelled. -
TKH-3466An internal call to unlock the vault for an OAuth2 client is now ignored when recording API version usage. This call would give the impression that an OAuth2 client always uses the latest API version. -
TKH-3469The application server was upgraded to WildFly 37. -
TKH-3479Members of a group selected for extra authorisation can no longer try to start audits for the groups they perform authorisation for, if they do not have these permissions. -
TKH-3483The version of Saltstack is now fixed to prevent upgrades to incompatible versions. -
TKH-3484We've made some minor improvements to our automated Azure/Entra provisioning tests. -
TKH-3489TKH-3509Accidentally accessing the quick search on the dashboard while activating a group is no longer possible, preventing an error when the group is activated. -
TKH-3494When trying to log in to an incorrectly configured SAML2 application, the user should now end up at a proper error page, instead of an internal error page. -
TKH-3498We now handle WebAuthn keys returning incorrect PRF values, preventing an error when trying to unlock the vault with such a key. Since opening the vault with that key is no longer possible, we reset the related state and so we can try to link it again for PRF. -
TKH-3501The list of permissions for an OAuth2 client is now searchable and filterable, so it is usable even if the client has many permissions. -
TKH-3502Input checks were corrected on the API for moving and sharing vault records. -
TKH-3505Requesting technical or profile administration for a group now once again shows a feedback message indicating the request was successfully created. -
TKH-3507Canceling a password synchronisation flow should no longer lead to an endless loop when subsequently trying to start password recovery for that same password. -
TKH-3514Authentication failures caused by an expired secret on Entra were not flagged as fatal, causing KeyHub to think the linked system was fully operational while it was actually broken.
Visit the Topicus KeyHub Manual
Here you can find the complete manual to the latest version of Topicus KeyHub.


