We're proud to announce Topicus KeyHub 19.3. This release brings syslog log streaming capabilities to the appliance. Also, our password recovery system has been enhanced to allow full self service password recovery. Two new provisioning schemes were added to the Azure Active Directory provisioning, introduced in 19.1. Lastly our group classifications, also introduced in 19.1, received several new options. And, as usual, a large number of smaller changes and bug fixes are included in this release.
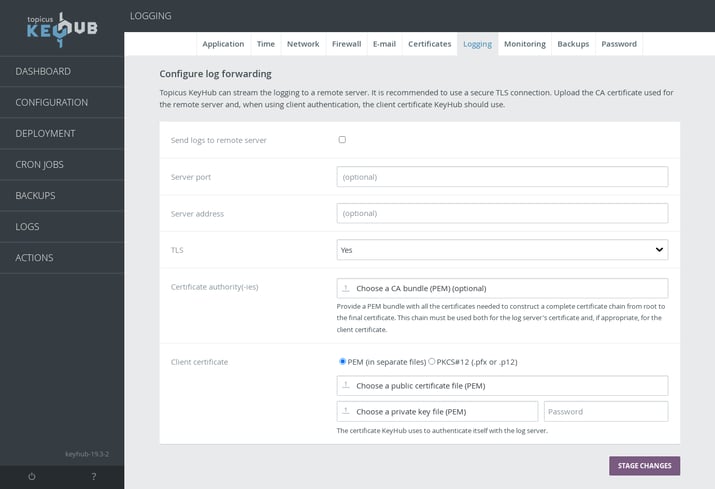
Log streaming
TKH-1547 TKH-2046 The entire logging infrastructure of the Topicus KeyHub appliance has been renewed. Logging of the Topicus KeyHub application is now performed through a centralized syslog container and forwarded to the syslog daemon on the host. The daemon on the host can be configured to forward the logs to a log streaming service for secure, near real time storage.
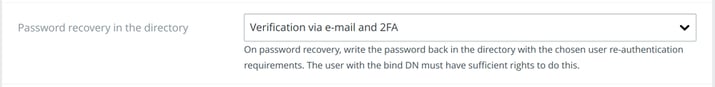
Full self-service password recovery
TKH-1972 Our password recovery on AD has been extended to allow the newly chosen password to be written back to the directory. This gives the possibility to provide full self-service password recovery via Topicus KeyHub. This password recovery can be used together with social recovery and when using a helpdesk group. Verification of the authenticity of the recovery request can be configured to be done via 2FA or e-mail or both.
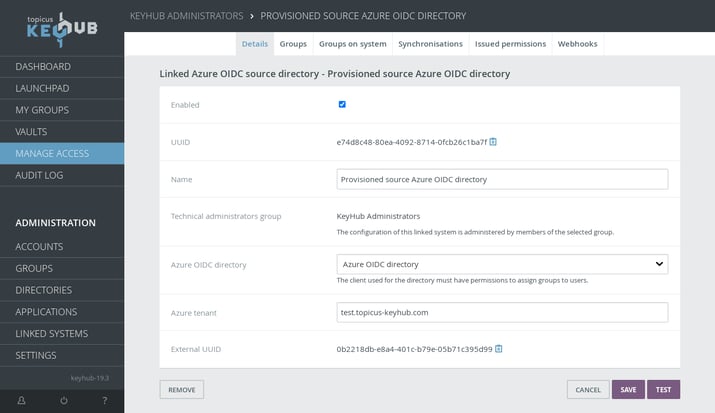
Azure source directory provisioning
TKH-1958 TKH-1959 New provisioning schemes are implemented that allow source directory provisioning on Azure Active Directory. This will allow Topicus KeyHub to dynamically assign existing users to groups in an Azure tenant. This option can also be combined with an on-premise Active Directory when using Azure Active Directory Connect.
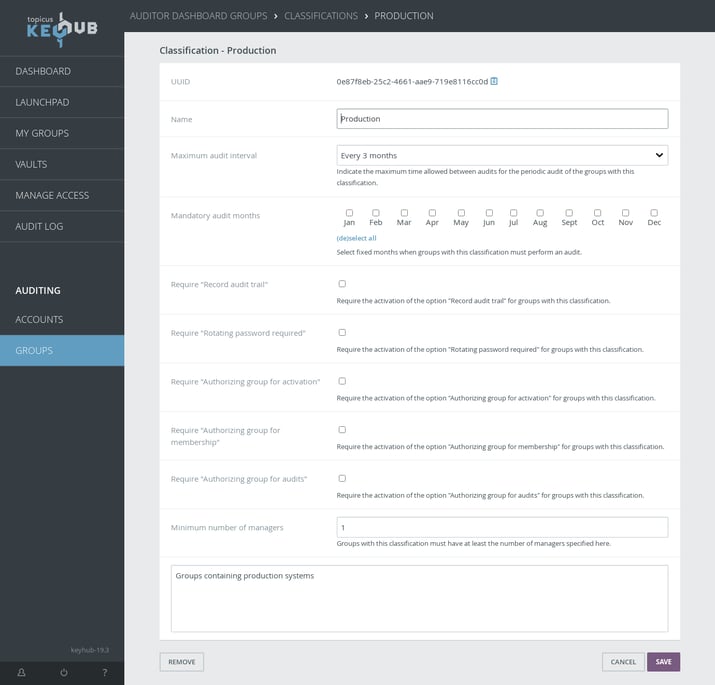
Requirements via group classifications
TKH-1977 TKH-1986 TKH-2027 TKH-2028 TKH-2029 Many new options were added to group classifications, making it possible to put restrictions on most group settings. Managers of groups with these classifications will automatically receive a notification when their group does not meet the requirements.
Small improvements
The following smaller improvements and bug fixes were made:
TKH-1576It is now possible to specify a hint for new group names, for example a pattern.TKH-1739New rules are enforced when handling cascading requests that prevent the same user to be involved in a single chain of requests more than once.TKH-1775It is now possible to disable social recovery or all recovery on a specific vault.TKH-1839Topicus KeyHub now sends notifications per e-mail when a user's authentication information changes in a significant way.TKH-1867The settings for the firewall in the appliance manager are now grouped together.TKH-1906The e-mails for social recovery now mention that a second approval is required.TKH-1921It is now possible to search groups on their UUID.TKH-1923TKH-1925New options are available for generating thesAMAccountnameattribute on Active Directory and changes are synced for existing users.TKH-1934It is now possible to retrieve a generated password via the REST API.TKH-1936Shared vault records no longer trigger a notification on the dashboard when they expire. Only the original vault record triggers such a notification.TKH-1937A button was added to trigger a test mail from the appliance manager.TKH-1951A different group than KeyHub administrators can now be configured to handle requests for creating new groups, enabling technical administration and/or removing groups.TKH-1955A CSV export was added for group memberships via the auditor groups dashboard.TKH-1967All groups now automatically get a default classification assigned.TKH-1974For groups with high traffic, the audit records can now be hidden from the audit trail on users' dashboards to reduce noise.TKH-1978A system-wide retention period can now be configured for the audit log.TKH-1994Pgpool-II was upgraded to 4.3.1.TKH-1998Secret shares used for password recovery are now synced more often, and are immediately invalidated when a user leaves the helpdesk or KeyHub administrators group.TKH-2002The application server was upgraded to WildFly 26.0.1.TKH-2007A client application can now be immediately granted access to vaults of groups it creates.TKH-2008It is now possible to request static provisioning when requesting to add a group to a group on a linked system.TKH-2010Names can now be 255 characters long throughout the entire application.TKH-2011An attributeactivewas added that can be used for custom attribute scripts that indicates if that group is currently enabled for the account.TKH-2012An issue was fixed when a vault containing a shared vault record became inaccessible, for example when the group was deleted.TKH-2014It is now possible to setup authorization for groups using the group itself to do the authorization.TKH-2015Logs are now rotated using the date of the contents, rather than the date of rotation.TKH-2016The login flow was improved to prevent the user from having to enter the password twice under some circumstances.TKH-2020An error was fixed that could occur when trying to logon to the appliance manager using SSO.TKH-2021The toolsdigandnslookupare now installed by default in the appliance to assist with debugging networking issues.TKH-2023Acceptance releases are now made available in a separate folder in our downloads directory.TKH-2025The SaltStack FQDNs grains were disabled to prevent SaltStack from making many reverse DNS lookup calls for internal IP addresses.TKH-2026The initialization of the distributed device code registry was fixed to prevent possible issues when running in a cluster.TKH-2030When starting an audit from the notification on the dashboard, an existing draft is opened, if present, instead of starting a new audit.TKH-2036A CSV export for accounts was added to the auditor accounts dashboard.TKH-2037Sorting of accounts on two factor authentication status was fixed.

